Our focus is on supporting all technology needs of small & medium businesses.

Through our managed services products and use of highly reliable equipment, we bring enterprise-class reliability to our clients.
Since 2000
Force a Shortcut to Open in a Specific Browser
To force a shortcut to open in a specific browser, you can create the shortcut in this format:
“Application path” space URL
Chrome "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.apple.com (more…)
Extended Security Updates for Windows 10
The Extended Security Updates (ESU) program is Microsoft’s paid service that delivers critical and important security patches to Windows 10 devices after official support ends on October 14, 2025. It’s designed to help organizations and individuals stay protected while they plan their transition to Windows 11. Windows 10 ESU is a practical solution for those who need more time to transition. (more…)
Comparing AI Tools: ChatGPT vs. Microsoft Copilot
These free AI tools offer tremendous value, by enhancing productivity and providing innovative solutions to complex problems. Both tools leverage the powerful GPT-4 model created in September of 2021, but they offer different features and functionalities. Let’s dive into a comparison to understand their strengths and unique capabilities. (more…)
Microsoft Groups Explained
Microsoft now has 6 types of groups! How do you know which type to use? Below are descriptions of each.
- Microsoft 365 Groups are used for collaboration between users, both inside and outside your company. They include collaboration services such as SharePoint and Planner. Microsoft Teams uses Microsoft 365 Groups for membership.
- Shared mailboxes are used when multiple people need access to the same mailbox, such as a company information or support email address.
Snapdrop – Transfer Files Between Any Device
Snapdrop allows users on the same network to quickly transfer files or send messages across all platforms. It uses a peer-to-peer (P2P) connection, making the data transfer very fast, and does not use Internet bandwidth or upload files to a server. To use it simply navigate to snapdrop.net on any two devices that are connected to the same Wi-Fi or wired network. (more…)
Multi-factor authentication
Multi-factor authentication (MFA) is an authentication technique that requires a user to present at least two factors that prove their identity.
- Something you know: A password.
- Something you have: A cellphone or keycard that can verify your identity.
- Something you are: Fingerprints or some other biometric data.
Dell Proximity Sensor.
Dell has added a feature on laptops that can make them act a bit strange. The proximity sensor watches you at all times. When you turn away it locks your PC. To turn this off go to Start Menu > Dell Optimizer > Proximity Sensor > Disable it. (more…)
Open Database Connectivity
Open Database Connectivity (ODBC) is designed to expose database capabilities via SQL. It improves the analytics process by giving users real-time access to data from multiple sources. Data can be transformed, within applications such as Excel and PowerBI, into reports and dashboards. Excel macros and scripting languages like PowerShell can automate the creation and distribution of reports via email, web page, or as saved files. (more…)
Web Searching 101
Boolean search
Utilizes special words or symbols to limit, widen, or define the scope of your search.
These include: AND, OR, NOT, and NEAR, as well as the symbols + (add) – (subtract) ” ” (quote).
| Boolean Operator | Symbol | Explanation | Example |
| AND | + | All words must be present in the results | football AND nfl |
| OR | Results can include any of the words | paleo OR primal | |
| NOT | – | Results include everything but the term that follows the operator | diet NOT vegan |
| NEAR | The search terms must appear within a certain number of words of each other | swedish NEAR minister |
Creating PDF Forms
A document can be easily converted to a fillable PDF form using either Adobe Acrobat Pro DC or Bluebeam Revu eXtreme (this feature is not available with Revu CAD or Revu Standard). If you are starting with a Word or Excel file, first convert that to a PDF, then follow these instructions:
(more…)
File Format & Missing Data
When collaborating on a document in the cloud, it is advisable to use common fonts. A custom font loaded on your local computer will be replaced when the recipient either does not have the font installed or opens the file in their browser-based Apps. This can lead to substantial changes in the layout of the document. (more…)
Keyboard Shortcuts
Using keyboard shortcuts will greatly enhance your productivity.
| Ctrl + | Action | Ctrl + | Action | Ctrl + | Action |
| b | Bold | c | Copy | a | Select all |
| u | Underline | x | Cut | z | Undo |
| i | Italic | v | Paste | y | Redo |
Searching in Outlook
 Use: AND, NOT, OR, <, >, =, operators (must be typed in all CAPS) to refine your search.. (more…)
Use: AND, NOT, OR, <, >, =, operators (must be typed in all CAPS) to refine your search.. (more…)
Verizon Call Filter
For Verizon customers, this app does a good job of blocking unsolicited calls. It provides real-time alerts and automatically blocks known offenders. The$3 subscription is not necessary for the basic level of protection.
iOS Database issues
After updating your iOS you may experience issues such as:
- Attachments not downloading.
- Calendar invites showing up as .ics files.
- Contact searches running very slow.
- Unread items showing incorrect count.
- Email downloading only the first few lines. (more…)
Microsoft Teams 101
 Teams is a great tool for real-time collaboration. It allows your office to call, chat and meet one place. Chats are persistent and can be secured to limit access. (more…)
Teams is a great tool for real-time collaboration. It allows your office to call, chat and meet one place. Chats are persistent and can be secured to limit access. (more…)
Multiple GPU Best Performance
 Workstation class laptops usually have two GPUs. The onboard Intel integrated GPU and a dedicated NVIDIA graphics card. When this is the case you need to make sure that your high-performance applications use the NVidia GPU, rather than the low-performance Intel integrated GPU.
Workstation class laptops usually have two GPUs. The onboard Intel integrated GPU and a dedicated NVIDIA graphics card. When this is the case you need to make sure that your high-performance applications use the NVidia GPU, rather than the low-performance Intel integrated GPU.
To ensure optimal application performance make the following adjustment: (more…)
Connect a mouse to your iPad
 Beginning with iOS 13 you can connect a Bluetooth mouse or Bluetooth keyboard & mouse combo to your iPad. Here are the steps:
Beginning with iOS 13 you can connect a Bluetooth mouse or Bluetooth keyboard & mouse combo to your iPad. Here are the steps:
- Go to settings > Accessibility > AssistiveTouch > Devices > Bluetooth Devices
- Place your device in pairing mode and select it from the iPad menu.
- Go back to AssistiveTouch and turn it on.
Identifying Nefarious Links
 In order to protect yourself on the Internet, you need to be proficient at locating and identifying domain names. This is because, emails and attachments can be used to redirect you to sites that are loaded with bad content. Make sure you can:
In order to protect yourself on the Internet, you need to be proficient at locating and identifying domain names. This is because, emails and attachments can be used to redirect you to sites that are loaded with bad content. Make sure you can:
- Verify the email sender.
- Verify any link contained in the message or within an attachment before clicking on it. (more…)
Grandparent Scam with a Twist
 The “Grandparent Scam” is a particularly disturbing scam perpetrated on the elderly. The criminal contacts the Grandparent, pretending to be a grandchild in trouble with the law or in desperate need of cash for a medical bill. They then claim that the matter cannot be discussed with other family members (red flag). Victims report receiving calls late at night, adding confusion and a sense of urgency. The preferred mechanism of money movement is wire transfer (red flag), and now via courier, sent to the victims home. (more…)
The “Grandparent Scam” is a particularly disturbing scam perpetrated on the elderly. The criminal contacts the Grandparent, pretending to be a grandchild in trouble with the law or in desperate need of cash for a medical bill. They then claim that the matter cannot be discussed with other family members (red flag). Victims report receiving calls late at night, adding confusion and a sense of urgency. The preferred mechanism of money movement is wire transfer (red flag), and now via courier, sent to the victims home. (more…)
Relative Paths and Linked Files
 Applications like InDesign and AutoCAD interlink files as you create content. This allows teams to share workloads, provides more efficient file storage and adds greater stability to the software platforms. These linked files can create an issue when multiple entities work on the same file or when content is moved to a new location. The solution to this problem is to use relative paths. (more…)
Applications like InDesign and AutoCAD interlink files as you create content. This allows teams to share workloads, provides more efficient file storage and adds greater stability to the software platforms. These linked files can create an issue when multiple entities work on the same file or when content is moved to a new location. The solution to this problem is to use relative paths. (more…)

KeePass Touch
This is the mobile version of Keepass, our recommended desktop password management tool. You can use iTunes on your PC or Mac to transfer your password database to your iOS device periodically. This will give you mobile access to your passwords without ever placing them at risk in the cloud. This can also serve as a backup location for your Keepass database. (more…)
Grammarly
 Grammarly is a writing assistant that can spell-check your web-based content as you write. It can be loaded as a firefox browser plugin for free. It offers advanced functionality, with a monthly subscription, to evaluate your writing in the areas of tone, engagement, clarity, and grammar.
Grammarly is a writing assistant that can spell-check your web-based content as you write. It can be loaded as a firefox browser plugin for free. It offers advanced functionality, with a monthly subscription, to evaluate your writing in the areas of tone, engagement, clarity, and grammar.
Common Fonts
 When creating an e-mail signature in Outlook or sharing a word or excel file, it is important to remember that fonts are not common across all platforms. If you use a font that does not exist on the recipient’s device, your signature or file appearance will change as the font you selected is replaced with a default font. This is mitigated on web-based platforms (e.g., a web site or blog) by using fonts that load to the user’s device in real-time from the cloud (1000 to choose from). (more…)
When creating an e-mail signature in Outlook or sharing a word or excel file, it is important to remember that fonts are not common across all platforms. If you use a font that does not exist on the recipient’s device, your signature or file appearance will change as the font you selected is replaced with a default font. This is mitigated on web-based platforms (e.g., a web site or blog) by using fonts that load to the user’s device in real-time from the cloud (1000 to choose from). (more…)
The Edge of WiFi
 When you have a weak wireless signal, you can try and boost it in a couple of ways:
When you have a weak wireless signal, you can try and boost it in a couple of ways:
- Make sure the wireless access point (WAP) closest to you is not obstructed. Clear away any dense objects within a foot of the device. You might also reposition it to boost the signal.
- Make sure your device in not in power save mode (yellow battery icon on iOS). It can be disabled in Settings > Battery > Low Power Mode: set to off. (more…)
Positive Pay
 A business may be held liable for all or a substantial portion of any loss when checks are stolen or altered. Positive Pay is an automated check fraud detection service offered by most banks. It matches the payee, check number, and dollar amount of each check presented for payment against a list of checks issued from your accounting system. All three components of the check must match exactly or the check will not be paid. (more…)
A business may be held liable for all or a substantial portion of any loss when checks are stolen or altered. Positive Pay is an automated check fraud detection service offered by most banks. It matches the payee, check number, and dollar amount of each check presented for payment against a list of checks issued from your accounting system. All three components of the check must match exactly or the check will not be paid. (more…)

Avoiding Cyber Fraud
Tips, from the FBI, to avoid becoming a victim of cyber fraud:
Do Not
- Do not give unknown, unverified persons remote access to devices or accounts.
- Do not communicate with unsolicited email senders.
- Do not act in haste. Criminals create a sense of urgency to produce fear and lure the victim into immediate action. (more…)
Battery Life & Lifespan
There is a great deal involved in maximizing the performance of your laptop or phone battery. GPS, Temperature and screen brightness all play a role. This Page from Apple details how to optimize each device.
The Traveling WiFi Circus
 Whether you are in a hotel, airport, or coffee shop, WiFi can be spotty. The most common cause is the requirement for you to agree to an acceptable use policy on each device. This must be done before you can connect to your email or VPN. To do this, launch your browser and go to a new page. At this point, you will be redirected to accept an agreement, or in some cases pay for access. Once you have joined one of these restricted networks, your device will always automatically reconnect in the future; (more…)
Whether you are in a hotel, airport, or coffee shop, WiFi can be spotty. The most common cause is the requirement for you to agree to an acceptable use policy on each device. This must be done before you can connect to your email or VPN. To do this, launch your browser and go to a new page. At this point, you will be redirected to accept an agreement, or in some cases pay for access. Once you have joined one of these restricted networks, your device will always automatically reconnect in the future; (more…)
iOS 13 Preview
Apple announced the new features of iOS 13 More here… Do not be the first to upgrade. Turn off Automatic Updates: Settings > General > Software Update > Automatic Updates > Off
Real ID
 Your current Illinois driver’s license will not be accepted at airports, military bases and secure federal facilities after Oct. 1, 2020. You can obtain a REAL ID card or use a passport after that time. To see what documents you need to apply for a REAL ID, visit the REAL ID Interactive Checklist. All Driver Services facilities are issuing REAL IDs, with the exception of mobile units and express facilities. To check your license look for a gold star at the top right. (more…)
Your current Illinois driver’s license will not be accepted at airports, military bases and secure federal facilities after Oct. 1, 2020. You can obtain a REAL ID card or use a passport after that time. To see what documents you need to apply for a REAL ID, visit the REAL ID Interactive Checklist. All Driver Services facilities are issuing REAL IDs, with the exception of mobile units and express facilities. To check your license look for a gold star at the top right. (more…)
This icon can ruin your iOS
 Hackers are using the familiar Apple settings icon to trick users into hacking their own iOS devices. As I discussed in a previous post, this can permanently destroy your device. If you ever see the settings icon and a request to install, confirm or cancel, do not click any response presented. Rather, you should immediately close your app. If the message returns upon reopening the app, contact IT support. (more…)
Hackers are using the familiar Apple settings icon to trick users into hacking their own iOS devices. As I discussed in a previous post, this can permanently destroy your device. If you ever see the settings icon and a request to install, confirm or cancel, do not click any response presented. Rather, you should immediately close your app. If the message returns upon reopening the app, contact IT support. (more…)
USPS helps criminals read your mail
 The U.S. Postal Service just fixed a security weakness that allowed anyone who has an account at usps.com to view account details for some 60 million other users, and in some cases to modify account details on their behalf. This would have been less of an issue before they released their latest service called Informed Delivery, which allows users to see the exterior of their mail. With this information, criminals can access private details and target you for fraud.
The U.S. Postal Service just fixed a security weakness that allowed anyone who has an account at usps.com to view account details for some 60 million other users, and in some cases to modify account details on their behalf. This would have been less of an issue before they released their latest service called Informed Delivery, which allows users to see the exterior of their mail. With this information, criminals can access private details and target you for fraud.
Gift Card Scam
 The Internet Crime Complaint Center received an increase in the number of Business complaints requesting false requests to purchase gift cards. The victims receive either a spoofed email, a spoofed phone call or a spoofed text from a person in authority requesting the victim purchase multiple gift cards for personal or business reasons. (more…)
The Internet Crime Complaint Center received an increase in the number of Business complaints requesting false requests to purchase gift cards. The victims receive either a spoofed email, a spoofed phone call or a spoofed text from a person in authority requesting the victim purchase multiple gift cards for personal or business reasons. (more…)
Office 365’s New Look
Office has a new look if you are on Office 365. One advantage that Office 365 offers is real-time access to the ever growing list of features that the product receives on an ongoing basis. Microsoft has also released its on-premise version of Office 2019
Facebook 90M Hacked
 Attackers exploited a vulnerability in Facebook’s code that impacted “View As” a feature that lets people see what their own profile looks like to someone else. This allowed them to steal Facebook access tokens which they could then use to take over people’s accounts.
Attackers exploited a vulnerability in Facebook’s code that impacted “View As” a feature that lets people see what their own profile looks like to someone else. This allowed them to steal Facebook access tokens which they could then use to take over people’s accounts.
5G is here.
 The next generation of cellular known as 5G is being rolled out on October 1. Verizon is first in the world to provide a commercial 5G service, with plans for rapid broadband internet, and 5G mobility service More Here …
The next generation of cellular known as 5G is being rolled out on October 1. Verizon is first in the world to provide a commercial 5G service, with plans for rapid broadband internet, and 5G mobility service More Here …

FBI: Remote Desktop Compromised
Remote administration tools, such as Remote Desktop Protocol (RDP), as an attack vector has been on the rise since mid-late 2016 with the rise of dark markets selling RDP Access. Malicious cyber actors have developed methods of identifying and exploiting vulnerable RDP sessions over the Internet to compromise identities, steal login credentials, and ransom other sensitive information. (more…)
High Quality Voice Calls
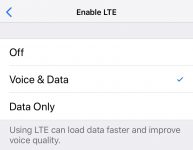 Your iPhone is capable of making higher quality voice calls with VoLTE. The quality improvement comes from increasing the bandwidth used to carry your voice, relative to a traditional cellular call. To enable this go to Settings > Cellular > Cellular Data Options > Enable LTE > Select Voice & Data
Your iPhone is capable of making higher quality voice calls with VoLTE. The quality improvement comes from increasing the bandwidth used to carry your voice, relative to a traditional cellular call. To enable this go to Settings > Cellular > Cellular Data Options > Enable LTE > Select Voice & Data

OneNote
OneNote is a virtual notebook, with incredible search capabilities, that synchronizes across all your devices and between multiple users in real time. A universal platform, it works on Windows, Mac, iOS, Android, and Online. Everything is stored as a separate element so markups can be removed, files or images can be saved or moved. Pages are a limitless whiteboard that can accept markups, tags, MS Office and 3rd party files, tables, images, video, audio, web elements and screen clippings. Here are our detailed instructions..
iPhone as backup ISP
Did you know you can use your iPhone, or iPad with cellular service, as a backup internet connection. You need to set it up before you loose Internet service. (more…)

Drones as a service
Capturing a unique perspective of a project is easier than ever with the use of a drone. Services such as Droners.io connect you with pilots from around the country, making capturing those images very easy and affordable. Costs range from $40-$150 depending on the scope of your project. (more…)
Security Awareness Training

Today the greatest threat to company security is the email vector. KnowBe4 provides security awareness training and simulated phishing attacks to test employee response to manage the continuing problem of social engineering.
Amazon Prices
Did you know that prices on Amazon change hourly. CamelCamelCamel.com tracks prices and can send alerts when they are at their lowest. Browser Plug-ins help simplify the service.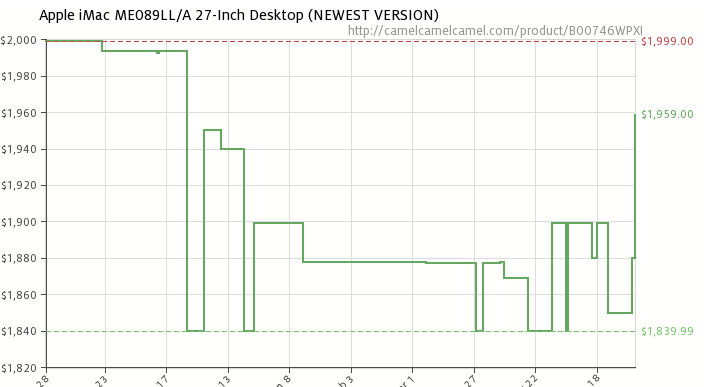
Never use Online Password Services
 There are a multitude of services that are built specifically for storing your passwords. I’d like to briefly delve into why it is foolish to use any of them.
There are a multitude of services that are built specifically for storing your passwords. I’d like to briefly delve into why it is foolish to use any of them.
First of all, there are specific instances of these sites being hacked, for obvious reasons. If you store all the gold in one bank, that’s where the robbers are going to go. (more…)
Fake Security Alerts
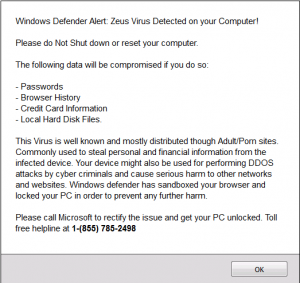 Should you get a pop-up like this one. Do not follow the advice in the window, and in particular, do not call the number in the window. Just close the browser immediately. DO NOT click on any part of the window, as this can trigger a virus installation. If the pop-up is preventing you from closing the browser, then reboot your computer. Also, make a mental note of the site you were visiting when the alert popped up. Very often it will be a news site or a content aggregation site; the type of site with lots of ads in the borders or strewn throughout the articles. (more…)
Should you get a pop-up like this one. Do not follow the advice in the window, and in particular, do not call the number in the window. Just close the browser immediately. DO NOT click on any part of the window, as this can trigger a virus installation. If the pop-up is preventing you from closing the browser, then reboot your computer. Also, make a mental note of the site you were visiting when the alert popped up. Very often it will be a news site or a content aggregation site; the type of site with lots of ads in the borders or strewn throughout the articles. (more…)
SketchUp Make is Illegal
 Sketchup Make is a free version of SketchUp, however, the license is not for commercial use. Employees of our clients will often unknowingly request that we install software that has similar limitations. These requests are not intended to do harm, but they can be costly. (more…)
Sketchup Make is a free version of SketchUp, however, the license is not for commercial use. Employees of our clients will often unknowingly request that we install software that has similar limitations. These requests are not intended to do harm, but they can be costly. (more…)
FBI: Internet-Connected Toys
 Consumer Notice: Internet-Connected Toys Could Present Privacy and Contact Concerns for Children
Consumer Notice: Internet-Connected Toys Could Present Privacy and Contact Concerns for Children
The FBI encourages consumers to consider cyber security prior to introducing smart, interactive, internet-connected toys into their homes or trusted environments. Smart toys and entertainment devices for children are increasingly incorporating technologies that learn (more…)
Server Storage
When specifying storage for a server-class machine, it’s important to understand that the drives within the system will be running 24/7 for the next 4-5 years. Because of this, the equipment used must be highly reliable. In order to enhance this reliability and fault tolerance, as well as the performance, various RAID (Redundant Array of Independent Disks) configurations are used.
- RAID 1 is a mirrored set of drives, should one fail, the second drive has a full copy of your data. In a normal operating state, the mirror also provides faster access when data is being read, as the data can be read from both drives simultaneously. RAID 1 is typically used for the operating system partition of the server.
- RAID 5: in this configuration, data is spread across (striping) 3-?? drives (depending on the chassis drive capacity) and a checksum is created on one additional drive. Should one drive fail, the data on the missing drive is calculated from the checksum and remaining drives. This is typically used for large capacity storage. It is not recommended to place more than 8 drives in a RAID 5 array.
- RAID 10: in this configuration, data is spread across 4-?? drives (depending on the chassis drive capacity) and a checksum is created on one additional drive. Should one drive fail, the data on the missing drive is calculated from the checksum and remaining drives. This is typically used for large capacity storage. It is not recommended to place more than 8 drives in a RAID 5 array.
- Global hot spare: an unused drive designated to rebuild the array in real time in the event of a failure. When one of the drives is predicted to fail, or it fails, this drive takes its place, ensuring the integrity of the data and continued operation in the event of failure.
Calculate Capacity
To calculate capacity for RAID 1 configurations, multiply the size of one of the drives by 0.8. This will gie you the usable data storage capacity for that drive.
To calculate capacity for RAID 5 configurations, subtract one from the number of drives in the RAID 5 array, then multiply that number times the capacity of each drive, then multiply that result by 0.8.
The global hot spare capacity is not included in either calculation, as it is unavailable for data storage.
Family Internet Safety
 Keeping your family safe on the Internet is a moving target. The Internet brings technology into our lives, but like the Gutenberg Press, its original purpose has been corrupted. If left unchecked, it will influence the very character of your children. To this end, I have a number of technologies and insights that can aid you in protecting your loved ones. In addition, scammers are aggressively targeting the elderly. (more…)
Keeping your family safe on the Internet is a moving target. The Internet brings technology into our lives, but like the Gutenberg Press, its original purpose has been corrupted. If left unchecked, it will influence the very character of your children. To this end, I have a number of technologies and insights that can aid you in protecting your loved ones. In addition, scammers are aggressively targeting the elderly. (more…)

KeePass
Passwords should never be stored in clear text, Excel or in the cloud. These are easy targets for viruses and hackers. KeePass is an open-source program that will store your passwords in an encrypted file on your Mac or PC. A pin or password is used to access your data. You can also load this directly to a mobile version of the program without the data ever touching the cloud. KeePass will actually speed your access to web-based accounts (more…)

Doceri
Doceri allows you to mirror and control any PC or Mac from a wirelessly connected iPad. It is also an interactive whiteboard that can be used to create a presentation, insert images, save and edit and record a screencast video that can be saved and shared. It works with any software as the makeups are actually being done in a separate space in front of your computers software. (more…)
Remote Access to Voicemail
If you need to retrieve voicemail from your cell phone, when you do not have access to your phone. Begin by calling your mobile number from another phone. When you hear your voicemail greeting, press the # key. This will interrupt the greeting and prompt you for your voicemail password. It is important that you know the voicemail password as you will need your cell phone to reset it. (more…)
4K Monitors & TVs
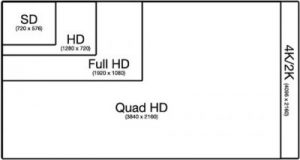
Resolution Comparison
4K monitors are taking over, but there are a number of pitfalls when implementing them.
Video cards: Even a lightweight card a NVidia Quadro NVS 295 (Passmark 103) will let you run at 4K resolution, but the PC is unusable. A more typical production card used by our architecture clients is the NVidia Quadro K2000 (Passmark 1672). The K2000 had no problem running a Samsung 75″ TV, and produces a fantastic picture. (more…)
Out of Office from your iPhone
Did you know you can enable your Out of office message from your iPhone (more…)



 A great
A great