 In order to protect yourself on the Internet, you need to be proficient at locating and identifying domain names. This is because, emails and attachments can be used to redirect you to sites that are loaded with bad content. Make sure you can:
In order to protect yourself on the Internet, you need to be proficient at locating and identifying domain names. This is because, emails and attachments can be used to redirect you to sites that are loaded with bad content. Make sure you can:
- Verify the email sender.
- Verify any link contained in the message or within an attachment before clicking on it.
Domain?
The domain is the two words after the double slash at the beginning of the URL “//” and directly in front of the first single forward slash “/”.
In the below examples the domain is “it-authority.com”
- ftp://lake.it-authority.com
- http://Disney.it-authority.com/fort-wilderness
- https://it-authority.com/ljhskdhfkubdfbbwd76873783/’jbdjnn?
- https://dhkjfddfdpofpododfd.dlfdfkoede.e.kfdklfdd..ddfkdokpoeepoepofpokfelel;fkelel;lfkelfkekefkelfk.elfkelkfl;ekl;fkeflkefl;kekf.it-authority.com/dfhkjdsajhj4lkjfkljdklfjldj34jkl4jrljrkljfldsmd.zzzxmmxcxsldkjfdkljafldkjjc,xx,cm,mcmdklclk34j3j34rj3kl3
Sometimes the change to a domain is subtle in order to trick you. The links below are NOT the same domain as above:
- http://Disney.iit-authority.com/fort-wilderness (extra “i”)
- http://it-authority.co/fort-wilderness (.co not .com)
Links
To prevent being redirected to a bad site you need to hover over all links before clicking on them. After a moment you will see the path or URL that you will be directed to, as in the picture below.

We can see that the message is from Symantec.com and the link is also from the same domain.
Try hovering over this link: www.apple.com
Who Sent It
When receiving an email asking you to take some action or follow a link, begin by looking at the sender’s email domain at the top of the message.
Let’s say you receive the following email:
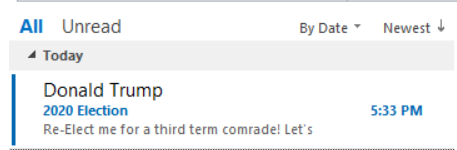
You open it and see the sender is: dtrump@whitehouse.gov. The name “Donald Trump” is unimportant as it can be faked. It “looks” to be legitimate, other than the spelling errors, but did you know that the reply address can be different than the sender’s!
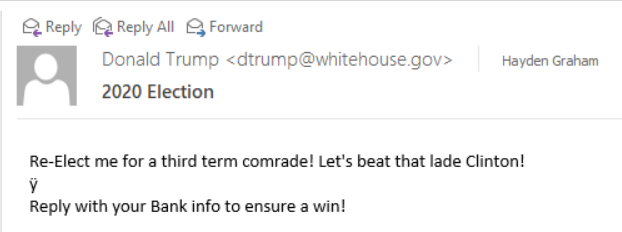
When you reply you now see: bhobama@whitehouse.ru.
Note some common mistakes such as unusual wording (comrade), spelling (lade not lady), strange characters (ÿ) and capitalization.
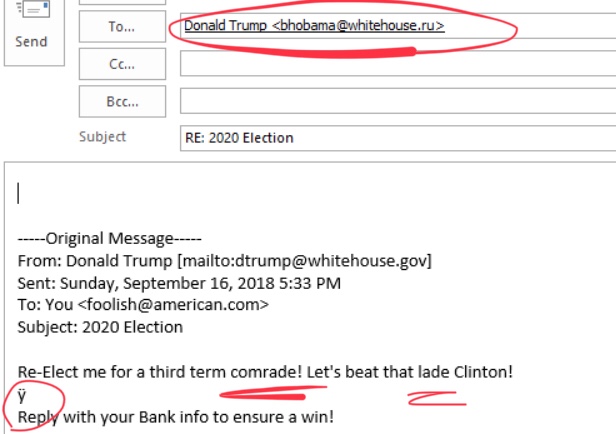
Often the sender’s information will be correct, but the attachments will try and get you to take some action, such as logon with an online account. You should never need to logon inorder to access a document.
More Examples
In this case, the hacker sends a photo of a real Apple receipt. The recipient sees the message is coming from what appears to be a legitimate Apple domain “storeapple.com“. Only after replying does the real source domain “ulahngasal.com” show up.
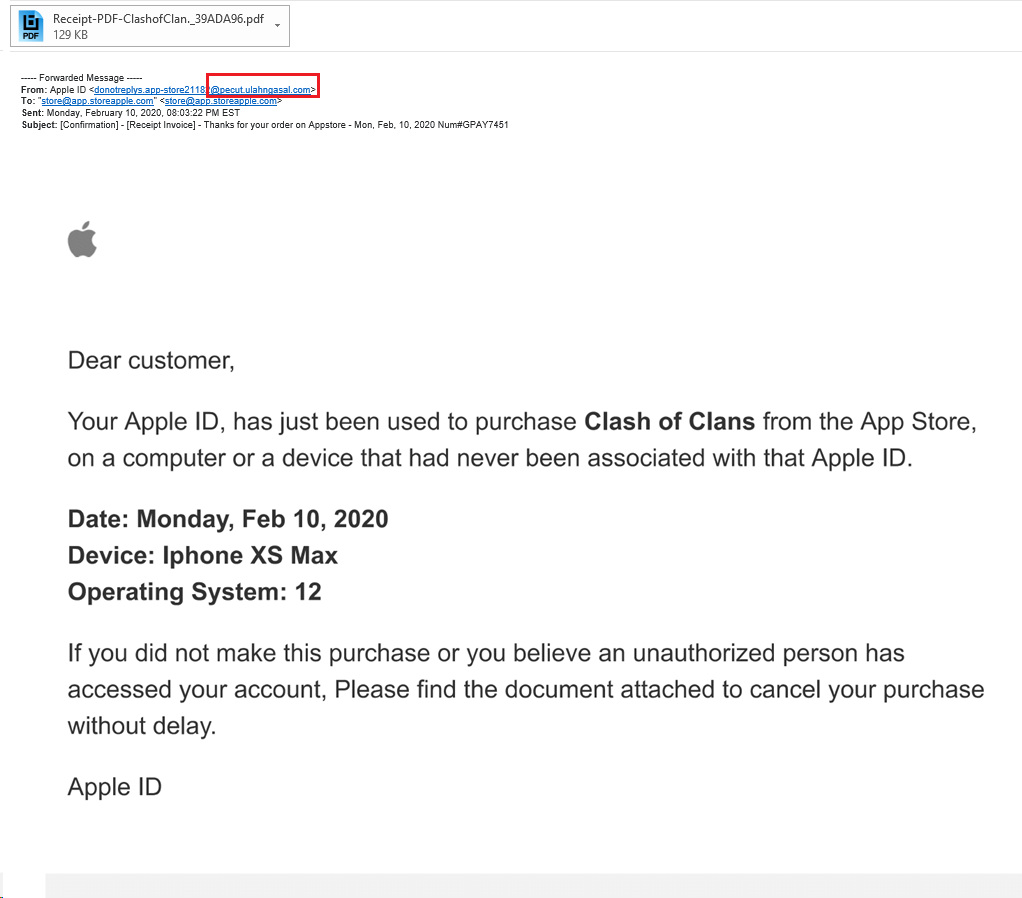
Opening the attachment they see another image of a real Apple receipt. When hovering over the message you see that it redirects to a “tiny url” that will take the user to a hacked site to infect the PC.

iOS:
It’s a little trickier on the iOS to view the domain, as you can only see the senders display name in the email- and this can be anything. In order to see the actual sender’s address, you have to tap on the display name in the “from” field at the top, then the email address will be displayed.
To view a link address, press and hold on the link. A window will open offering options. You will be able to view the full url at the top of the window.
Icons made by Eucalyp from www.flaticon.com
